Message Digest 5 (MD5) vs Secure Hash Algorithm 256 (SHA-256)
What is Hash Function?
Hash is a function that when it’s used to produce a particular output for every single input independent of time, machine power and device specification. According to the algorithm, output is always in fixed size. Even if the input size is changed, output size never does.
There are lots of Hash algorithms in cryptology. MD5 is one of them. All algorithms have the same magical specification which is irreversibility. Think about the billions of petabyte of data. When it goes into the hash function as a parameter, output is just 32 digits, 128-bits (commonly). So, we ever never ever can go back to the actual form, reversible is impossible. Designer of the MD5 Ron Rivest talk about decryption “MD5 is not an encryption algorithm, it is a message digest algorithm. There should be no feasible way to determine the input, given the output. That is one of the required properties of a message digest algorithm.”
As like humans have the hand signature, digital content have also an digital identity information. It’s called digest, output of hash or value.
Message Digest 5 (MD5)
MD5 is an algorithm to convert input data to digest. It’s not an encryption algorithm. Thus, decryption of the result is not possible. MD5 is designed by Math Professor Ron Rivest. In Rivest personal website, he does not suggest to use Hash functions, because Hash functions’ collision-resistance is weak and it has been proven mathematically in 2004.
If you need more collision-resistance in the cryptography we can use SHA-256 function as Rivest suggested. According to the D Rachmawati et al 2018 J. Phys.: Conf. Ser. 978 012116 research, MD5 has better performance than SHA-256 in millions of consistent data. It can be understood how MD5 is better, if algorithm has a weak collision-resistance, it contains the shortest path to create result value.
Secure Hash Algorithm (SHA-256)
First SHA function is SHA-2 has been designed by United States National Security Agency, published in 2001. SHA-256 has been published in 2008 by National Institute of Standards and Technology.
Considering the performance SHA-256 has a lower performance than MD5. Even if the complexity and calculation effort is equal to MD5, when input data is bigger to compute, average running time of both algorithm is different from each other.
Comparison Average Running Time
Following chart consists of three sample files to calculate MD5 and SHA-256 result values. Big Oh notations of both two algorithms are the same which is O(N). However, ignored inner calculations increases SHA-256 running time.
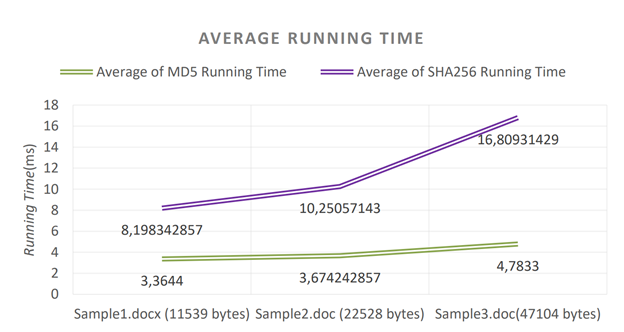
D Rachmawati et al 2018 J. Phys.: Conf. Ser. 978 012116, Figure 1.0
Share
Leave a Comment
You can share your questions, comments or criticisms about this post with me. Your e-mail address will not be shared with anyone.

Comments (0)
There are no comments for this post yet. Be the first to comment.